How Information and Network Protection Protects Versus Arising Cyber Dangers
In a period marked by the fast evolution of cyber threats, the value of information and network safety and security has never been more noticable. As these hazards end up being extra intricate, understanding the interaction between information safety and network defenses is necessary for minimizing risks.
Comprehending Cyber Risks
The ever-evolving nature of technology consistently presents brand-new vulnerabilities, making it imperative for stakeholders to stay alert. Individuals might unknowingly succumb to social design tactics, where opponents manipulate them right into disclosing sensitive information. Organizations face unique challenges, as cybercriminals usually target them to manipulate beneficial data or disrupt procedures.
Furthermore, the surge of the Internet of Points (IoT) has actually broadened the attack surface area, as interconnected gadgets can function as entrance points for opponents. Recognizing the importance of durable cybersecurity methods is essential for minimizing these risks. By cultivating a thorough understanding of cyber companies, individuals and risks can apply reliable methods to protect their electronic possessions, making sure durability in the face of a significantly intricate hazard landscape.
Secret Parts of Information Security
Making certain information safety calls for a complex approach that encompasses numerous crucial parts. One fundamental aspect is information security, which changes delicate info into an unreadable style, obtainable just to authorized users with the suitable decryption secrets. This acts as a critical line of protection against unauthorized access.
Another important element is access control, which manages who can check out or manipulate information. By carrying out stringent customer verification procedures and role-based access controls, companies can lessen the risk of expert dangers and information breaches.
Additionally, information covering up strategies can be used to safeguard delicate details while still permitting its usage in non-production environments, such as screening and advancement. fft perimeter intrusion solutions.
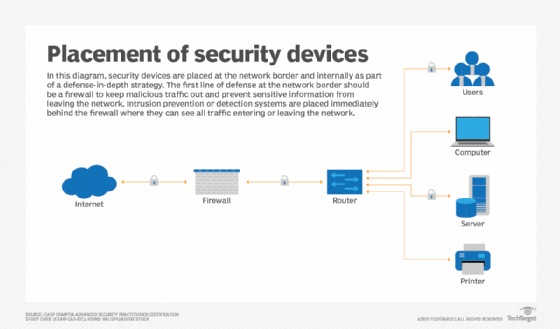
Network Safety And Security Approaches
Implementing robust network protection strategies is vital for protecting a company's digital infrastructure. These techniques involve a multi-layered approach that includes both software and hardware options created to protect the stability, confidentiality, and availability of data.
One crucial component of network safety and security is the deployment of firewall softwares, which function as a barrier between relied on inner networks and untrusted external networks. Firewall programs can be hardware-based, software-based, or a combination of both, and they assist filter outgoing and inbound web traffic based on predefined protection policies.
Additionally, invasion discovery and prevention systems (IDPS) play a vital role in keeping track of network traffic for questionable activities. These systems can alert managers to prospective violations and act to reduce risks in real-time. Regularly patching and upgrading software application is likewise critical, as susceptabilities can be exploited by cybercriminals.
Furthermore, applying Virtual Private Networks (VPNs) makes sure protected remote gain access to, encrypting information transferred over public networks. Finally, segmenting networks can lower the attack surface area and contain possible violations, restricting their impact on the general facilities. By taking on these methods, organizations can efficiently strengthen their networks versus arising cyber hazards.
Best Practices for Organizations
Establishing best methods for organizations is essential in preserving a solid safety and security posture. A detailed technique to information and network safety and security begins with normal risk assessments to determine susceptabilities and possible dangers.
Additionally, constant worker training and understanding programs are crucial. Staff members need to be enlightened on identifying phishing attempts, social engineering tactics, and the importance of adhering to safety and security protocols. Routine updates and patch management for software program and systems are likewise important to shield against known susceptabilities.
Organizations need to establish and examine incident response prepares to ensure preparedness for possible breaches. This consists of establishing clear interaction channels and roles throughout a safety occurrence. In addition, information file encryption ought to be utilized both at remainder and in transportation to secure delicate details.
Finally, carrying out routine audits and compliance checks will aid make sure adherence to relevant guidelines and recognized plans - data cyber security fft perimeter intrusion solutions. By adhering to these ideal methods, organizations can dramatically boost their strength versus arising cyber dangers and secure their critical properties
Future Trends in Cybersecurity
As companies navigate an increasingly complicated digital landscape, the future of cybersecurity is poised to advance dramatically, driven by changing and arising innovations danger paradigms. One prominent fad is the integration of synthetic knowledge (AI) and artificial intelligence (ML) right into protection structures, enabling real-time hazard detection and response automation. These technologies can evaluate huge amounts of data to determine anomalies and possible violations a lot more efficiently than standard methods.
Another important trend is the rise of zero-trust style, which calls for continual confirmation of user identities and device protection, no matter their location. This strategy decreases the risk of expert risks and boosts defense versus outside attacks.
Furthermore, the raising fostering of cloud services demands durable cloud safety approaches that attend to distinct vulnerabilities associated with cloud environments. As remote job ends up being a permanent fixture, safeguarding endpoints will additionally end up being vital, causing an elevated concentrate on endpoint discovery and action (EDR) services.
Lastly, regulatory compliance will certainly proceed to form cybersecurity techniques, pressing organizations to adopt extra rigid information defense steps. Accepting these patterns will be important for organizations to fortify their defenses and navigate the developing landscape of cyber risks efficiently.
Conclusion
To conclude, the application of robust information and network safety procedures is vital for organizations to safeguard against emerging cyber hazards. By using encryption, accessibility control, and efficient network protection techniques, companies can considerably minimize susceptabilities and secure sensitive information. Adopting ideal methods better boosts durability, preparing organizations to encounter developing cyber obstacles. As cybersecurity remains to advance, staying educated regarding future fads will be critical in maintaining a solid protection against possible threats.
In a period marked by the rapid evolution of cyber risks, the relevance of information and network protection has never been more pronounced. As these risks come to be a lot more complex, recognizing the interaction in between information security and network defenses is important for alleviating risks. Cyber threats include a wide variety of harmful activities intended at endangering the privacy, integrity, and availability of networks and data. A thorough technique to data and network safety and security starts with regular danger analyses to identify vulnerabilities and possible dangers.In final thought, the application of durable information and network safety measures is vital for companies to protect versus emerging cyber risks.